Privacy and security are critical elements to ensure that health information technology properly serves patients and keeps their health data secure. To attain these goals, the Health Insurance Portability and Accountability Act (HIPAA) sets minimum federal standards for both privacy and security of protected health information (PHI). HIPAA applies to organizations and individuals who submit claims electronically; since the vast majority of pharmacies and pharmacists submit claims electronically, they are covered entities under the HIPAA privacy and security rules. Covered entities have a number of legal obligations under both rules.
Definition of PHI
PHI is broadly encompassing as defined by HIPAA1:
Protected health information means individually identifiable health information:
(1) Except as provided in paragraph (2) of this definition, that is:
(i) Transmitted by electronic media;
(ii) Maintained in electronic media; or
(iii) Transmitted or maintained in any other form or medium.
Many records kept in pharmacies meet the definition of PHI, including prescription records, billing records, patient profiles, and counseling records. Hence, pharmacy systems must satisfy HIPAA standards for privacy and security. Note that PHI is not restricted to electronic media or transmissions; an oral communication of individually identifiable health information constitutes PHI.
HIPAA has a rule that permits disclosure of PHI for health care operations, treatment, and payment. This exclusion covers the vast majority of clinical uses of PHI. Most other disclosures would require specific patient consent; however, there are a small number of additional exceptions, including public health reporting.
Pharmacy Privacy Requirements
The HIPAA privacy rule is applicable to most day-to-day pharmacy operations.2 In general, all PHI must be kept private, and only the minimum necessary information should be disclosed for health care operations and payment. This rule does not exclude exchange of clinical information with other caregivers who are actively involved in the patient’s care. For example, a pharmacist may discuss clinical information with a physician or nurse practitioner who is prescribing a medication for the patient. This use of PHI falls under normal health care treatment. However, the pharmacist may not discuss PHI with a third party who has no treatment relationship or health insurance coverage relationship with the patient, unless there is patient consent. This rule applies to all types of communication including oral, written, and electronic.
Many states have more stringent privacy rules than HIPAA, particularly in the arenas of behavioral health, human immunodeficiency virus, substance abuse, and genetic information. There are other federal rules that are stricter than HIPAA, such as the federal regulations that govern substance abuse treatment records. There is also a federal rule governing the use of Medicaid information. HIPAA does not preempt the more stringent state rules. Therefore, pharmacies need to be aware of their own state rules in addition to HIPAA’s, and must always follow the rule that is more stringent. In some cases, a state law might require specific patient consent for release of certain types of information.
Security With Flexibility
The HIPAA security rule provides a flexible framework for implementation of security measures.3 Some requirements are mandatory, whereas others are “addressable,” meaning that they can be implemented by the organization in a manner that is consistent with the organization’s functionality, infrastructure, and resources. See Table 1 for specific rules.
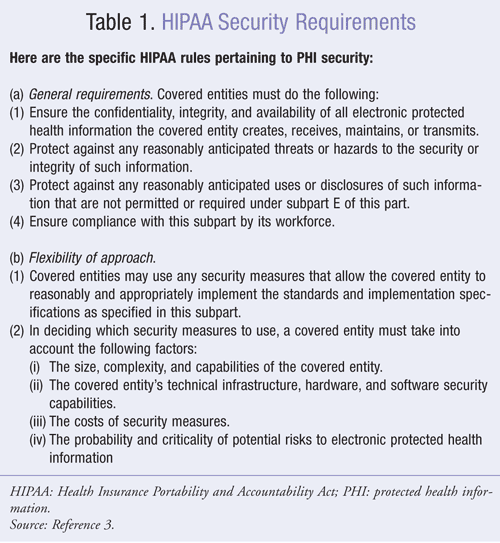
The security rule places a heavy emphasis on risk analysis, especially as applicable to electronic systems. Pharmacies should work with their vendors to identify and address appropriate security options. A common example of risk that is easily addressed involves the transmission of data over an open network, such as the Internet. In such instances, the data should be encrypted to ensure privacy. For example, if a pharmacy transmits data from one store to another over the Internet, the transmission should be encrypted to avoid eavesdropping. Standard encryption software is now readily available, so this should be a standard practice. Acceptable encryption algorithms are available through the National Institute of Standards and Technology (NIST) of the United States Department of Commerce.
Another area of typical concern for security is with wireless networks within a workplace. For example, if several computers in a pharmacy are on a wireless network, then care should be taken to ensure that the encryption function of the wireless network is actually activated. Communications over an unencrypted wireless network are easily intercepted by anyone near the pharmacy. The storage of PHI data on a hard drive, especially on portable devices such as laptop computers, is an area of great concern. Many breaches of privacy have occurred as a result of stolen laptops. There are various ways to address this risk, including encryption of hard drives. In the past, this has been a somewhat expensive option, but is now within reach of most organizations. Another option is to use the laptop as a tool to view data that exist on a secure server, but are never stored on the laptop.
Secure Passwords
Other common security concerns that can be addressed in a risk analysis relate to authentication of computer users and access controls. In general, each user of a computer system should have his or her unique authentication credentials. In many instances, the organization will determine that a user name and password are sufficiently strong so as to ensure that only authorized individuals can gain access to the system. However, when used as a single factor for authentication, passwords are considered by NIST to be a relatively weak protection.4 If passwords are used, they should not be shared, and should be of sufficient strength that they cannot easily be guessed. Passwords should generally contain a combination of alpha and numeric characters, or special characters, so as to increase their complexity. Passwords should not be posted near a computer, as this totally defeats their utility as a safeguard. The security rule requires the use of unique user identification. Future enhancements of HIPAA under the Health Information Technology for Economic and Clinical Health Act of 2009 (HITECH) may require audit trails to document who accessed PHI on any given date. User names and passwords should never be shared; otherwise it will not be possible to employ unique identifiers to correctly attribute a data access event to a specific person.
If an organization determines that stronger authentication requirements should be implemented, then a two-factor approach can be used. The general approach to two-factor authentication is to rely on two of the following factors: (1) something you know (e.g., a password); (2) something you are (e.g., a biometric characteristic); and (3) something you have (e.g., a hard token holding a digital certificate).One example of a hard token is a device that generates a one-time number that must be entered with the password. This is known as a one-time password hard token. Other types of hard tokens include those holding digital certificates that are activated by a password.
Systems that employ all three factors for authentication are more secure than systems that employ only one or two factors. One sophisticated approach to authentication implements a public key infrastructure (PKI) in which individuals are issued their own digital certificates by a certificate authority. This approach employs two asymmetric keys. The individual holds a private key on a hard token, and his or her identity can be confirmed using a public key.
In addition to assessing its approach to authentication of computer users, the organization should assess its approach to access of functions and data on the system. One approach to this is known as role-based access. In this scenario, an authenticated pharmacist would have access to certain types of data and functionality based on his or her role as a pharmacist, whereas a technician might have access to a different set of data and system functionality. Access rights should be customized to support the legitimate business needs of the authenticated user.
The organization is also required to review physical safeguards for computer systems. Those include physical access to hardware, environmental controls, emergency power backups, and disaster recovery procedures.
Electronic Health Records
HITECH was enacted to promote the widespread adoption and meaningful use of electronic health records (EHRs) and related technologies. In support of this goal, the act introduced a number of provisions that greatly strengthen HIPAA. On July 8, 2010, the U.S. Department of Health and Human Services (HHS) released a proposed rule to implement these new provisions. When the final rule is released, organizations will be given a specific timeframe to come into compliance. In addition, many of the HITECH statutory provisions became effective on February 18, 2010.
Among other things, HITECH requires covered entities that implement an EHR to provide an audit trail accounting for all disclosures of information. At this time, it is not clear how the term electronic health record will be defined in this context. HITECH also requires covered entities to provide electronic copies of PHI maintained in an EHR to the patient upon request. For this purpose, an EHR is very broadly defined in the proposed rule as any electronic data set. If this provision is maintained in the final rule, then pharmacies will be required to provide electronic copies of their computer data sets to patients upon request. In addition, covered entities must honor an individual’s request not to share data with a health plan if the individual is paying the full cost of the service.
Significantly, HITECH extends the reach of HIPAA to business associates of covered entities. Hence, any business associate that contracts with a pharmacy will now be held to the same privacy standards as the pharmacy and will be subject to the same criminal and civil penalties for violations.
The principles discussed above with respect to authentication of computer users are also relevant to the authentication of prescribers on e-prescribing systems. The Drug Enforcement Agency (DEA) issued an interim final rule permitting e-prescribing of controlled substances.5 In order to maintain the security of these e-prescriptions, a number of very stringent requirements are imposed by the rule, which the software industry is gearing up to implement.
One of the requirements is that the prescriber must sign off on the prescription using a two-factor authentication protocol. The permitted factors are two of the following: (1) a password, (2) a biometric, (3) a hard token (either a cryptographic module or a one-time password device). In addition, under the interim final rule, practitioners have the option to use a private cryptographic key to digitally sign the prescription. The pharmacy software is then required to apply a public key to decrypt the prescription, thus confirming the identity of the prescriber. The associated digital certificate must be obtained from a certification authority that is cross-certified with the federal PKI policy authority. The private key associated with the digital certificate must be stored on a hard token.
Conclusion
In summary, a variety of federal rules, including the HIPAA privacy and security rules, HITECH and its associated proposed rule, and the DEA interim final rule for e-prescribing of controlled substances, set the stage for adoption of health information technology while maintaining the privacy and security of patient and prescription data. A number of technical advances including strong encryption algorithms and digital certificates hold great promise as tools for implementation of many provisions in these rules. Pharmacists and pharmacy managers need to become familiar with these concepts, as most pharmacists and pharmacies are covered entities under HIPAA, and will be held responsible for complying with the various federal rules.
REFERENCES
1. U.S. Department of Health and Human Services. Office of Civil Rights. HIPAA Administrative Simplification. Combined Regulation Text of All Rules. 45 CFR Parts 160, 162, and 164.
www.hhs.gov/ocr/privacy/hipaa/
2. U.S. Department of Health and Human Services. Office of the Secretary. 45 CFR Parts 160 and 164. Standards for privacy of individually identifiable health information. Office for Civil Rights, HHS. Final rule. Federal Register. 2002;67(157):53182-53273.
3. U.S. Department of Health and Human Services. Office of the Secretary. 45 CFR Parts 160, 162, and 164. Health insurance reform: security standards. Centers for Medicare & Medicaid Services (CMS), HHS. Final rule. Federal Register. 2003;68(34)8334-8381.
4. Burr WE, Dodson DF, Polk WT. NIST Special Publication 800-63 Version 1.0.2. Electronic authentication guideline.http://csrc.nist.gov/
Accessed September 18, 2011.
5. U.S. Department of Justice. Drug Enforcement Administration.21 CFR Parts 1300, 1304, 1306, and 1311. Electronic prescriptions for controlled substances. Interim final rule. Federal Register. 2010;75(61):16236-6319.
To comment on this article, contact rdavidson@uspharmacist.com.





