US Pharm. 2022;47(5):34-38.
Pharmacies collect personally identifiable information (PII) and protected health information (PHI ) from customers to dispense prescription drugs, bill and obtain payment for prescription drugs, and to maintain appropriate prescription records.1,2 Many pharmacy records meet the definition of PII and PHI, including but not limited to a customer’s name, address, email address, phone number, date of birth, social security number, prescriptions, prescription labels, patient profiles, patient-counseling records, claims and insurance information, and health diagnoses. Federal and state data security laws impose duties upon pharmacies to maintain the privacy of personally identifiable information, and thus pharmacies should conduct their operations in a manner to protect patient PII and PHI, as required by applicable laws.3
Data Breach Ransomware Risks for Pharmacies
In late 2020, the federal Cybersecurity and Infrastructure Security Agency (CISA) issued an alert in conjunction with the U.S. Department of Health and Human Service (HHS) and the Federal Bureau of Investigation (FBI) indicating that they had credible information of an increased and imminent cybercrime threat to healthcare providers and recommending that healthcare providers take timely and reasonable precautions to protect their networks from such threats.4
Nearly 50 million people in the U.S. had their PHI involved in a data breach during 2021, a threefold increase in 3 years, according to a Politico analysis of the latest HHS data breach information.5 The number of phishing attacks against pharmacies and hospitals increased 189% from December 2020 to February 2021, and the trend is likely to continue in 2022.6
Data breaches expose pharmacies to significant risk and place them under scrutiny by regulators, payors, and customers. Consequences of a data breach may include significant financial loss, reputational damage, operational downtime, government investigations, and legal actions. IBM Security recently published its 2021 Data Breach Cost Report, which shows that healthcare data breach average costs are $9.42 million per incident and healthcare ransomware attacks costs an average of $4.62 million per incident.7 Cyberattacks and ransomware in the pharmacy sector present a fundamental threat to the financial viability of pharmacies, thus pharmacies must take timely and reasonable actions to protect their networks from cyberattacks and ransomware.
Several factors make pharmacies a target for cybercriminals, including the types of PII and PHI that they maintain and recent digital transformations with regard to electronic health records, electronic prescribing, and telemedicine. In addition, many pharmacies have outdated computer systems and have not undertaken basic data security steps such as encryption and monitoring their networks 24/7 for intrusions.
Recent Pharmacy Data Breaches and Legal Actions
Pharmacy data breaches, ransomware, and/or cybersecurity attacks have recently been reported by Surecare Specialty Pharmacy, GenRx Pharmacy, Ravkoo Online Pharmacy, and BioPlus Specialty Pharmacy.9,11,13 Multiple class-action lawsuits (hereinafter collectively referred to as the lawsuits) against BioPlus Specialty Pharmacy Services (BioPlus) are illustrative of the potential risks for pharmacy data breaches.12,13
On December 10, 2021, BioPlus reported to the HHS that a hacking breach on or around October 25, 2021, involving a network server had affected the PHI of 350,000 individuals. Data potentially compromised in the attack included names, contact information, dates of birth, medical record numbers, health insurance and claims information diagnoses, prescription information, and Social Security numbers. All affected individuals were notified of the data breach and offered a free 12-month subscription to credit-monitoring services.14
The BioPlus data breach resulted in lawsuits generally alleging that the pharmacy was negligent due to failure to comply with industry-standard data security practices as well as federal and state laws and regulations governing data security and privacy, including security of PII and PHI. One of the lawsuits alleges that class members’ PII is currently for sale to criminals on the dark Web and that class members’ PII are at a serious, immediate, and ongoing risk. The lawsuits seek financial damages as well as improvements to BioPlus’ security practices.15
Compliance With Federal and State Laws and Industry-Standard Data Security Practices
Pharmacies can reduce the risk of cyberattacks and ransomware by implementing industry-standard data security practices and complying with applicable federal and state laws. A summary of key industry-standard data security practices and applicable legal requirements is provided below.
HIPAA Privacy and Security Compliance
The Health Insurance Portability and Accountability Act of 1996 (HIPAA), which is applicable to pharmacies, protects PHI and imposes penalties for failure to take action to prevent the disclosure of such information.16 HHS has issued guidance addressing how healthcare organizations may apply standards under the HIPAA Security Rule to prevent and recover from ransomware attacks.17
HIPAA Security Requirements for Ransomware Infections
The Security Management Process standard of the Security Rule includes requirements for all pharmacies to conduct an accurate and thorough risk analysis of the potential risks and vulnerabilities to the confidentiality, integrity, and availability of the electronic PHI (ePHI) that pharmacies create, receive, maintain, or transmit; and they must also implement security measures sufficient to reduce those identified risks and vulnerabilities to a reasonable and appropriate level.18
The HIPAA Security Rule requires implementation of security measures that can help prevent the introduction of malware, including ransomware. The required security measures include:
• Implementing a security-management process, which includes conducting a risk analysis to identify threats and vulnerabilities to ePHI and implementing security measures to mitigate or remediate those identified risks;
• Implementing procedures to guard against and detect malicious software;
• Training users on malicious software protection so they can assist in detecting malicious software and know how to report such detections; and
• Implementing access controls to limit access to ePHI to only those persons or software programs requiring access.19
Ransomware Attacks Are HIPAA Security Incidents
Security incident procedures, including procedures for responding to and reporting security incidents, are also required by HIPAA.20 A pharmacy’s security incident procedures should prepare it to respond to various types of security incidents, including ransomware attacks. The presence of ransomware (or any malware) on a pharmacy’s computer network is a security incident under the Security Rule and should be addressed as required by the pharmacy’s security-incident procedures, which should include processes to:
• Detect and conduct an initial analysis of the ransomware;
• Contain the impact and propagation of the ransomware;
• Eradicate the instances of ransomware and mitigate or remediate vulnerabilities that permitted the ransomware attack and propagation;
• Recover from the ransomware attack by restoring data lost during the attack and returning to “business as usual” operations; and
• Conduct postincident activities, which could include a deeper analysis of the evidence to determine if the entity has any regulatory, contractual, or other obligations as a result of the incident (such as providing notification of a breach of PHI), and incorporating any lessons learned into the overall security management process.21
Data Backup and Contingency Plans to Address Ransomware
The HIPAA Security Rule requires pharmacies to implement a data backup plan and maintain an overall contingency plan. Activities that must be part of a pharmacy’s contingency plan include: disaster recovery planning, emergency operations planning, analyzing the criticality of applications and data to ensure all necessary applications and data are accounted for, and periodic testing of contingency plans to ensure readiness to execute such plans and provide confidence they will be effective.22
NIST Cybersecurity Framework for Ransomware Risk Management
The National Institute of Standards and Technology (NIST) has released a draft Cybersecurity Framework Profile for Ransomware Risk Management (the Profile) to help companies prevent, respond, and recover from ransomware attacks.23 The Profile outlines basic measures that can be implemented to improve defenses against ransomware attacks. These include the use of antivirus software, multifactor authentication, external email flagging and scanning, spam filtering, patch management and software updates, complex password management, firewall configuration, network segmentation, blocking access to known ransomware sites, only permitting authorized apps to be used, restricting the use of personally owned devices or apps, prohibition on the use of accounts with administrative privileges, and conducting employee security awareness training.24
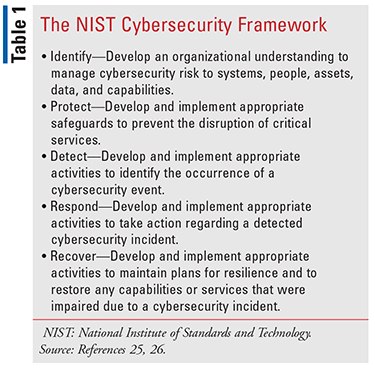
The Profile should be used in conjunction with the NIST Cybersecurity Framework (the Framework), which organizes cybersecurity activities into five key functions and explains how each function can help to prevent and respond to cyberattacks.25 The five Framework cybersecurity functions are shown in TABLE 1.
CISA Ransomware Best Practices
CISA has published recent guidance, Protecting Sensitive and Personal Information from Ransomware-Caused Data Breaches, which includes best practices for preventing cybercriminals from accessing computer networks and outlines steps that can be taken to protect sensitive data and recommends the adoption of the following measures to prevent and detect data breaches and/or ransomware attacks.27,28
Prevention
Backups. Maintain offline, encrypted backups of data and regularly test your backups.
Cyber Incident Response Plan. Create, maintain, and exercise a security incident response plan and notification procedures for security incidents.
Address Internet Vulnerabilities
Vulnerability Scanning. Conduct regular Internet-vulnerability scanning.
Software Patches/Updates. Regularly patch/update software and operating systems to latest versions.
Device Configuration. Properly configure devices with security features enabled.
Remote Desktop Services. Employ best practices for use of remote desktop services.
Server Messages. Disable or block Server Message Block protocol outbound.
Address Phishing Vulnerabilities
Security Awareness Training. Implement a cybersecurity user awareness and training program that includes guidance on how to identify and report suspicious activity.
Email Filters. Implement filters at the email gateway to filter out emails with known malicious indicators and block suspicious Internet Protocol (IP) addresses at the firewall.
Message Authentication. Implement Domain-based Message Authentication, Reporting and Conformance policy and verification.
Disable Macro Scripts. Disable macro scripts for Microsoft Office files transmitted via email, as such macros can be used to deliver ransomware.
Address Malware Vulnerabilities
Update Software. Ensure antivirus and antimalware software and signatures are up to date. Additionally, turn on automatic updates for both solutions.
Application Directory. Use application directory allow listing on devices to ensure that only authorized software can run and all unauthorized software is blocked.
Intrusion Detection System. Implement an intrusion-detection system to detect command and control activity and other potentially malicious network activity.
Address Third-Party Vendor Vulnerabilities
Vendor Vetting Process. Review and consider vendor cybersecurity practices and use contract language to formalize your security requirements.
FTC Cybersecurity Recommendations
The Federal Trade Commission (FTC) has authority over businesses that collect health information under the FTC Act and has issued guidance on cybersecurity.29 The FTC Act prohibits unfair and deceptive acts and practices. The FTC may bring enforcement actions against healthcare organizations that make deceptive claims about the use or disclosure of health data or engage in unfair practices, such as a failure to take reasonable security measures to protect health data. The FTC guidance indicates that failure to implement appropriate defenses against ransomware could constitute a violation of the FTC Act and recommends the adoption of the following measures to prevent and detect data breaches and/or ransomware attacks:
• Access to Data. Control access to all data and restrict access to sensitive data. Implement steps such as separate user accounts to limit access to the places where personal data are stored or to control who can use particular databases.
• Passwords and Authentication. Use multifactor authentication and require complex and unique secure passwords and authentication for all devices. Prevent authentication bypass and require employees to store passwords securely.
• Secure Passwords and Authentication. Store sensitive personal information securely and protect it during transmission. Use strong encryption to secure confidential material during storage and transmission. Encrypt devices and other media that contain PII or PHI.
• Segment and Monitor Networks. Use tools such as firewalls to segment your network, and use intrusion detection and prevention tools to monitor the network for malicious activity.
• Remote Access Security. Secure remote access to your network, including restricting connections to specified IP addresses or granting temporary, limited access.
• Service Provider Security Measures. Only select vendors that meet security standards and include contract provisions that require vendors to maintain compliance.
• Maintain Current Security Policies and Procedures. Update security policies and procedures to ensure that they are current, and address new vulnerabilities that may arise.
• Secure Paper, Physical Media, and Devices. Securely store all PII and PHI and keep safety standards in place when data are en route. Protect devices that process personal information, and dispose of sensitive data securely.
• Training. Train all staff and create a culture of security by implementing regular training at defined intervals.
Conclusion
The recent pharmacy data breaches and lawsuits emphasize the importance for pharmacies to take appropriate actions to prevent cyberattacks and ransomware. Reasonable and appropriate actions include compliance with applicable federal and state laws and adoption and implementation of healthcare industry standards for cybersecurity. The HIPAA Safe Harbor Act amended the HITECH Act to require OCR to consider the cybersecurity standards, guidelines, best practices, methodologies, procedures, and processes that had been implemented for at least 12 months prior to the data breach when considering fines, penalties, and other sanctions for healthcare organizations.30 The cybersecurity compliance costs and cybersecurity insurance costs are nominal compared with the costs for noncompliance.
The content contained in this article is for informational purposes only. The content is not intended to be a substitute for professional advice. Reliance on any information provided in this article is solely at your own risk.
REFERENCES
1. Personally identifiable information generally incorporates information that can be used to distinguish or trace an individual’s identity, either alone or when combined with other personal or identifying information. 2 C.F.R. § 200.79.
2. Health information, including diagnoses, treatment information, medical test results, and prescription information, is considered protected health information under the Health Insurance Portability and Accountability Act (“HIPAA”) Privacy and Security requirements.
3. National Conference of State Legislatures. State laws related to digital privacy. www.ncsl.org/research/telecommunications-and-information-technology/state-laws-related-to-internet-privacy.aspx. Accessed April 22, 2022.
4. Cybersecurity and Infrastructure Security Agency. Alert (AA20-302A): ransomware activity targeting the healthcare and public health sector. Original release date: October 28, 2020; last revised: November 2, 2020. www.cisa.gov/uscert/ncas/alerts/aa20-302a. Accessed April 22, 2022.
5. Leonard B. Health data breaches swell in 2021 amid hacking surge, POLITICO analysis finds. Politico. March 23, 2022. www.politico.com/news/2022/03/23/health-data-breaches-2021-hacking-surge-politico-00019283. Accessed April 22, 2022.
6. Davis J. Pharmacy, hospital phishing attacks spike 189% amid vaccine rollout. Health IT Security. March 24, 2021. https://healthitsecurity.com/news/pharmacy-hospital-phishing-attacks-spike-189-amid-vaccinerollout. Accessed April 22, 2022.
7. IBM. How much does a data breach cost? IBM Cost of Data Breach Report 2021. https://www.ibm.com/security/data-breach. Accessed April 22, 2022.
8. Calculated HIPAA. Ransomware attacks reported by Surecare Specialty Pharmacy, Blue Shield of California, and Blue Cross of California. November 29, 2021. [Surecare Specialty Pharmacy was the victim of a ransomware attack on August 16, 2021. Surecare’s investigation confirmed on August 31, 2021, that files containing 8,412 patients’ protected health information may have been accessed and/or exfiltrated prior to the deployment of ransomware, and a review of the encrypted files confirmed they contained patient names, addresses, dates of birth, health insurance information, prescription information, and Social Security numbers.] www.calhipaa.com/ransomware-attacks-reported-by-surecare-specialty-pharmacy-blue-shield-of-california-and-blue-cross-of-california/. Accessed April 22, 2022.
9. Walker J. GenRx Pharmacy ransomware attack leads to HIPAA data breach disclosure. The Daily Swig: Cybersecurity News and Views. December 30, 2020. [GenRx Pharmacy was the victim of a ransomware attack on September 27, 2020. GenRx discovered that hackers accessed and removed the PHI of 137,110 patients, including their first and last name, address, phone number, date of birth, gender, allergies, medication list, health plan information, and prescription information.]
https://portswigger.net/daily-swig/genrx-pharmacy-ransomware-attack-leads-to-hipaa-data-breach-disclosure. Accessed April 22, 2022.
10. Cyber Intel Mag. US digital pharmacy Ravkoo linked data breach to AWS portal vulnerability. January 7, 2022. [Ravkoo Online Pharmacy was the victim of a cyberattack on September 27, 2021. Ravkoo discovered that cybercriminals accessed the PHI of 105,000 patients, including their full name, mail address, phone number, prescription information, and limited medical information.] https://cyberintelmag.com/attacks-data-breaches/us-digital-pharmacyravkoo-linked-data-breach-to-aws-portal-vulnerability/. Accessed April 22, 2022.
11. McKeon J. BioPlus Specialty Pharmacy faces lawsuit over healthcare data breach. Health IT Security. January 17, 2022. [BioPlus Specialty Pharmacy was the victim of a cyberattack in October 2021. BioPlus discovered that hackers accessed the PHI of 350,000 patients, including, contact information, dates of birth, medical record numbers, health insurance and claims information, medical diagnoses, prescription information, and Social Security numbers.] https://healthitsecurity.com/news/bioplus-specialty-pharmacy-faces-lawsuit-over-healthcare-data-breach. Accessed April 22, 2022.
12. BioPlus Specialty Pharmacy Services LLC is a national specialty drug pharmacy that offers services for people with hepatitis C, Crohn’s disease, multiple sclerosis, rheumatoid arthritis, psoriasis, psoriatic arthritis, cancer, and other chronic, complex conditions.
13. Gilbert v. BioPlus Specialty Pharmacy Services, LLC, Case No. (6:21cv02158), US District Court for the Middle District of Florida, filed December 27, 202; Bryan et al. v. BioPlus Specialty Pharmacy Services, LLC, Case No. (6:22-cv-00030), US District Court for the Middle District of Florida, filed January 5, 2022; Smith et al v. BioPlus Specialty Pharmacy Services, LLC, Case No. (6:22-cv-00136), US District Court for the Middle District of Florida, filed January 21, 2022; Graden et al. v. BioPlus Specialty Pharmacy Services, LLC, Case No. (6:22-cv00159), US District Court for the Middle District of Florida, filed January 26, 2022.
14. Id.
15. Id.
16. 45 CFR § 160.103.
17. U.S. Department of Health and Human Services; Office for Civil Rights. Fact sheet: ransomware and HIPAA. July 11, 2016. www.hhs.gov/sites/default/files/RansomwareFactSheet.pdf. Accessed April 22, 2022.
18. HIPAA Security Rule (45 C.F.R. §§164.302-164.318).
19. Id.
20. See 45 C.F.R. 164.308(a)(6).
21. Id.
22. See 45 C.F.R. 164.308(a)(7).
23. Barker W, Scarfone K, Fisher W, Souppaya M. Cybersecurity framework profile for ransomware risk management (preliminary draft). https://csrc.nist.gov/publications/detail/nistir/8374/archive/2021-06-09. Accessed April 22, 2022.
24. HIPAA Journal. NIST releases draft guidance for ransomware risk management. June 22, 2021. www.hipaajournal.com/nist-releases-draft-guidance-for-ransomware-risk-management/. Accessed April 22, 2022.
25. Fisher B, Souppaya M, Barker WC, Scarfone K. Ransomware risk management: a cybersecurity framework profile. February 23, 2022. www.nist.gov/publications/ransomware-risk-management-cybersecurity-framework-profile. Accessed April 22, 2022.
26. Id.
27. CISA. Protecting sensitive and personal information from ransomware-caused data breaches. www.cisa.gov/sites/default/files/publications/CISA_Fact_Sheet-Protecting_Sensitive_and_Personal_Information_from_Ransomware-Caused_Data_Breaches-508C.pdf. Accessed April 22, 2022.
28. Stop Ransom Ware; CISA. Ransomware guide and ransomware prevention best practices. www.cisa.gov/stopransomware/ransomware-guide. Accessed April 22, 2022.
29. Federal Trade Commission. Sharing consumer health information? Look to HIPAA and the FTC Act. www.ftc.gov/business-guidance/resources/sharing-consumer-health-information-look-hipaa-ftc-act. Accessed April 22, 2022.
30. www.congress.gov/116/plaws/publ321/PLAW-116publ321.pdf.
To comment on this article, contact rdavidson@uspharmacist.com.






